- Cisco Anyconnect User Interface Startup
- Cisco Anyconnect Disable Automatic Selection
- Cisco Anyconnect Automatic Start
- Cisco Anyconnect Startup Disable
- Remove Cisco Anyconnect From Autostart
Temporarily disable your Cisco AnyConnect Secure Mobility Client by following these steps: From Windows Start, select Run and type msconfig.exe in the Run box. This will run the System Configuration app. In the System Configuration dialog box, select the Startup tab. For Windows 7, deselect Cisco AnyConnect Services. The Cisco AnyConnect Secure Mobility Client uses the Simple Certificate Enrollment Protocol (SCEP) to provision and renew a certificate as part of client authentication. Certificate enrollment using SCEP is supported by AnyConnect IPsec and SSL VPN connections to the ASA in the following ways.
Virtual private networks (VPN) allow users to access organization resources remotely, including from home, hotels, cafes, and more. In Microsoft Intune, you can configure VPN client apps on Android Enterprise devices using an app configuration policy. Then, deploy this policy with its VPN configuration to devices in your organization.
You can also create VPN policies that are used by specific apps. This feature is called per-app VPN. When the app is active, it can connect to the VPN, and access resources through the VPN. When the app isn't active, the VPN isn't used.

This feature applies to:
- Android Enterprise
There are two ways to build the app configuration policy for your VPN client app:
- Configuration designer
- JSON data
This article shows you how to create a per-app VPN and VPN app configuration policy using both options.
Note
Many of the VPN client configuration parameters are similar. But, each app has its unique keys and options. Consult with your VPN vendor if you have questions.

Before you begin
Android doesn't automatically trigger a VPN client connection when an app opens. The VPN connection must be started manually. Or, you can use always-on VPN to start the connection.
The following VPN clients support Intune app configuration policies:
- Cisco AnyConnect
- Citrix SSO
- F5 Access
- Palo Alto Networks GlobalProtect
- Pulse Secure
- SonicWall Mobile Connect
When you create the VPN policy in Intune, you'll select different keys to configure. These key names vary with the different VPN client apps. So, the key names in your environment may be different than the examples in this article.
The Configuration designer and JSON data can successfully use certificate-based authentication. If VPN authentication requires client certificates, then create the certificate profiles before you create the VPN policy. The VPN app configuration policies use the values from the certificate profiles.
Android Enterprise personally-owned work profile devices support SCEP and PKCS certificates. Android Enterprise fully managed, dedicated, and corporate-owned work profile devices only support SCEP certificates. For more information, see Use certificates for authentication in Microsoft Intune.
Per-app VPN overview
When creating and testing per-app VPN, the basic flow includes the following steps:
- Select the VPN client application. Before you begin (in this article) lists the supported apps.
- Get the application package IDs of the apps that will use the VPN connection. Get the app package ID (in this article) shows you how.
- If you use certificates to authenticate the VPN connection, then create and deploy the certificate profiles before you deploy the VPN policy. Make sure the certificate profiles deploy successfully. For more information, see Use certificates for authentication in Microsoft Intune.
- Add the VPN client application to Intune, and deploy the app to your users and devices.
- Create the VPN app configuration policy. Use the app package IDs and certificate information in the policy.
- Deploy the new VPN policy.
- Confirm the VPN client app successfully connects to your VPN server.
- When the app is active, confirm that traffic from your app successfully goes through the VPN.
Get the app package ID
Get the package ID for each application that will use the VPN. For publicly available applications, you can get the app package ID in the Google Play store. The displayed URL for each application includes the package ID.
In the following example, the package ID of the Microsoft Edge browser app is com.microsoft.emmx. The package ID is part of the URL:
For Line of Business (LOB) apps, get the package ID from the vendor or application developer.
Certificates
This article assumes your VPN connection uses certificate-based authentication. It also assumes you successfully deployed all the certificates in the chain needed for clients to successfully authenticate. Typically, this certificate chain includes the client certificate, any intermediate certificates, and the root certificate.
For more information on certificates, see Use certificates for authentication in Microsoft Intune.
When your client authentication certificate profile is deployed, it creates a certificate token in the certificate profile. This token is used to create the VPN app configuration policy.
If you’re not familiar with creating app configuration policies, see Add app configuration policies for managed Android Enterprise devices.
Use the Configuration Designer
Sign in to the Microsoft Endpoint Manager admin center.
Select Apps > App configuration policies > Add > Managed devices.
In Basics, enter the following properties:
Name: Enter a descriptive name for the policy. Name your policies so you can easily identify them later. For example, a good policy name is App config policy: Cisco AnyConnect VPN policy for Android Enterprise work profile devices.
Description: Enter a description for the policy. This setting is optional, but recommended.
Platform: Select Android Enterprise.
Profile type: Your options:
- All Profile Types: This option supports username and password authentication. If you use certificate-based authentication, don't use this option.
- Fully Managed, Dedicated, and Corporate-Owned Work Profile Only: This option supports certificate-based authentication, and username and password authentication.
- Personally-Owned Work Profile Only: This option supports certificate-based authentication, and username and password authentication.
Targeted app: Select the VPN client app you previously added. In the following example, the Cisco AnyConnect VPN client app is used:
Select Next.
In Settings, enter the following properties:
Configuration settings format: Select Use Configuration designer:
Add: Shows the list of configuration keys. Select all the configuration keys needed for your configuration > OK.
In the following example, we selected a minimal list for AnyConnect VPN, including certificate-based authentication and per-app VPN:
Configuration value: Enter the values for the configuration keys you selected. Remember, the key names vary depending on the VPN Client app you're using. In the keys selected in our example:
Per App VPN Allowed Apps: Enter the application package ID(s) you collected earlier. For example:
KeyChain Certificate Alias (optional): Change the Value type from string to certificate. Select the client certificate profile to use with VPN authentication. For example:
Protocol: Select the SSL or IPsec tunnel protocol of the VPN.
Connection Name: Enter a user friendly name for the VPN connection. Users see this connection name on their devices. For example, enter
ContosoVPN.Host: Enter the host name URL to the headend router. For example, enter
vpn.contoso.com.
Select Next.
In Assignments, select the groups to assign the VPN app configuration policy.
Select Next.
In Review + create, review your settings. When you select Create, your changes are saved, and the policy is deployed to your groups. The policy is also shown in the app configuration policies list.
Use JSON
Use this option if you don't have, or don't know all the required VPN settings used in the Configuration designer. If you need help, consult your VPN vendor.
Get the certificate token
In these steps, create a temporary policy. The policy won't be saved. The intent is to copy the certificate token. You'll use this token when creating the VPN policy using JSON (next section).
In the Microsoft Endpoint Manager admin center, select Apps > App configuration policies > Add > Managed devices.
In Basics, enter the following properties:
- Name: Enter any name. This policy is temporary, and won't be saved.
- Platform: Select Android Enterprise.
- Profile type: Select Personally-Owned Work Profile Only.
- Targeted app: Select the VPN client app you previously added.
Select Next.
In Settings, enter the following properties:
Configuration settings format: Select Use configuration designer.
Add: Shows the list of configuration keys. Select any key with a Value type of string. Select OK.
Change the Value type from string to certificate. This step lets you select the correct client certificate profile that authenticates the VPN:
Immediately change the Value type back to string. The Configuration value changes to a token
{{cert:GUID}}:Copy and paste this certificate token to another file, such as a text editor.
Discard this policy. Don't save it. The only purpose is to copy and paste the certificate token.
Create the VPN policy using JSON
In the Microsoft Endpoint Manager admin center, select Apps > App configuration policies > Add > Managed devices.
In Basics, enter the following properties:
- Name: Enter a descriptive name for the policy. Name your policies so you can easily identify them later. For example, a good policy name is App config policy: JSON Cisco AnyConnect VPN policy for Android Enterprise work profile devices in entire company.
- Description: Enter a description for the policy. This setting is optional, but recommended.
- Platform: Select Android Enterprise.
- Profile type: Your options:
- All profile types: This option supports username and password authentication. If you use certificate-based authentication, don't use this option.
- Fully Managed, Dedicated, and Corporate-Owned work profile only: This option supports certificate-based authentication, and username and password authentication.
- Personally-Owned Work Profile Only: This option supports certificate-based authentication, and username and password authentication.
- Targeted app: Select the VPN client app you previously added.
Olivetti driver. Select Next.
In Settings, enter the following properties:
- Configuration settings format: Select Enter JSON data. You can edit the JSON directly.
- Download JSON template: Use this option to download, and update the template in any external editor. Be careful with text editors that use Smart quotes, as they may create invalid JSON.
After you enter the values needed for your configuration, remove all settings that have
'STRING_VALUE'orSTRING_VALUE.Select Next.
In Assignments, select the groups to assign the VPN app configuration policy.
Select Next.
In Review + create, review your settings. When you select Create, your changes are saved, and the policy is deployed to your groups. The policy is also shown in the app configuration policies list.
JSON example for F5 Access VPN
Additional information
Next steps
When you are off campus, some of Illinois State University’s electronic services are unavailable to you unless you establish a VPN connection.
Cisco AnyConnect is an application that the University makes available to students, faculty, and staff for free which may be used to establish a VPN connection with the University from off campus.
NOTE: If you need to request and install the application on your computer, please skip to the section further below entitled Download and Install Cisco AnyConnect. If you already have the application installed and would like to know how to connect to it, please read the section immediately below entitled Connect to the Cisco AnyConnect VPN Client Once Downloaded. The instructions below are listed for both Windows and Mac machines, respectively.
Connect to the Cisco AnyConnect VPN Client Once Downloaded
Windows:
- Open the Cisco AnyConnect VPN client.
- Windows 8: On the Start screen, click Cisco AnyConnect Secure Mobility Client.
- Windows 10: Start > All Apps > Cisco > Cisco AnyConnect Secure Mobility Client.
- Alternatively, you can click Start and begin typing Cisco AnyConnect Secure Mobility Client and the application will show up. Click on the icon to start the application.
- Verify that the path in the field underneath “Ready to connect.” is VPN01.ILSTU.EDU.
- If the path name does not automatically appear, click the arrow to the right of the field and select VPN01.ILSTU.EDU from the drop down menu, or enter the path name manually.
- Click Connect.
Figure 1:
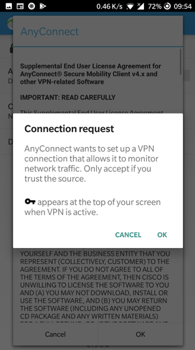
- When prompted, select the appropriate Group (Figure 1):
- To access most ISU resources, you will select –ISU-.
- Important: To access ISU Oracle or SQL database resources directly (via software such as Microsoft Access, Oracle SQL Developer, Microsoft SQL Management Studio, etc.), select DB-User_Access.
Note: When you attempt to connect, you may receive a prompt that tells you that Cisco AnyConnect is updating. Do not attempt to cancel this update, as this update will allow your VPN software to work.
Figure 2:
- Enter your ULID and password in the appropriate fields, then click OK.
- After a moment, an informational banner window will appear that typically says “Welcome to Illinois State University,” but could display a different, informational message.
- Click Accept.
You are now connected with the Cisco AnyConnect VPN client. A Cisco AnyConnecticon with a yellow, locked padlock will be visible in your system tray (in the lower-right corner of your desktop, next to the clock). This indicates that you are connected. If the icon appears without a padlock, this indicates you are no longer connected through VPN.
Mac OS X:
- Open the Cisco AnyConnect VPN client. Click Finder > Applications> Cisco > Cisco AnyConnect Secure Mobility Client.
Figure 3:
- Alternatively, you can search for the application in your “Dashboard” by simply clicking the rocket icon on your bottom toolbar. After that, start typing Cisco AnyConnect Secure Mobility Client and you will see the application. Click on the application to start the set-up process, or to access it once you’ve configured the settings properly.
Figure 4:
- Verify that the path in the field underneath “Ready to connect.” reads VPN01.ILSTU.EDU. If the field is empty, you will need to manually enter the file path exactly how it is shown in this article.
Figure 5:
- Click Connect.
- When prompted, select the appropriate Group (Figure 6):
- For most ISU resources, you will select –ISU-.
- Important: To access ISU Oracle or SQL database resources directly (via software such as Microsoft Access, Oracle SQL Developer, Microsoft SQL Management Studio, etc.), select DB-User_Access.
Figure 6:
- Enter your ULID and password when prompted to do so and click Connect.
- After a moment, an informational banner window will appear that typically says “Welcome to Illinois State University,” but could display a different, informational message.
- Click Accept.
You are now connected with the Cisco AnyConnect VPN client. A Cisco AnyConnect icon with a yellow, locked padlock is now in your system tray (in the lower-right corner of your desktop). This indicates that you are connected. If the icon appears without a padlock, this indicates you are no longer connected through VPN.
Disconnect from the VPN
Windows:
To disconnect from the VPN on a Window’s machine:
- Locate the Cisco AnyConnect VPN client icon and click on it. It is usually on your toolbar, but if it is not, here are some additional ways to find the application:
- Windows 8: On the Start screen, click Cisco AnyConnect Secure Mobility Client.
- Windows 10: Start > All Apps > Cisco > Cisco AnyConnect.
- Alternatively, you can click [Start] and begin typing Cisco AnyConnect Secure Mobility Client and the application will show up. Click on the icon to start the application so you can disconnect from the VPN.
Cisco Anyconnect User Interface Startup
- In the Cisco AnyConnect Secure Mobility Client pane, click Disconnect.
Figure 7:
- Close Cisco AnyConnect Secure Mobility Client.
You are now disconnected from VPN.
Mac OSX:
To disconnect from a VPN connection on Cisco AnyConnect on Mac running Mac OS X or later:
- Click on the Cisco AnyConnect icon in your Dock.
- Click Disconnect.
- Close Cisco AnyConnect Secure Mobility Client.
Figure 8:
You are now disconnected from VPN.
Download and Install Cisco AnyConnect for Windows or Mac OS X
Students, faculty, and staff may download the Cisco AnyConnect VPN Client for Windows or Mac OS X from the University IT Help portal by following the directions below:
Windows:
- Navigate to the IT Help portal (at ITHelp.IllinoisState.edu),
- Click Downloads in the middle of the screen.
- Under Cisco AnyConnect, select the version you would like to download. You will need to select the version that is compatible with your machine. You can choose either Windows or Mac.
- Click on Windows or Mac and log in with your ULID and password if prompted to do so. You will be directed to a form to request the download file be sent to you. You will need to fill out the required fields in the submission form. Once submitted, your request will be handled in the order it was received. Once approved, you will receive an email. You will then click Download Files and you may be navigated to a Central Login page where you will need to enter your ULID and password. Once you log in, click the file next to Attached Files.
NOTE: If you have never access Liquid Files (SendTo) before, you may see a log in page to log into Liquid Files itself. Instead, you will want to click the SSO Sign In button to be navigated to a Central Login page. You will enter your ULID and password. Upon logging in, you will need to accept some terms and conditions. Once you have done that, you will never be prompted again for an SSO sign in.
- Upon successfully downloading the installer, you will need to open the installer and follow the prompts.
Figure 9:
- Agree to the Terms and Conditions and proceed with the installation by clicking Accept. You may need to enter your computer’s profile credentials in order to accept the installation.
Figure 10:
- Once the software has finished downloading, click Finish to close out of the installation process. You can now access the VPN software.
Mac OS X:
- Navigate to the IT Help portal (at ITHelp.IllinoisState.edu),
- Click Downloads in the middle of the screen.
- Under Cisco AnyConnect, select the version you would like to download. You will need to select the version that is compatible with your machine. You can choose either Windows or Mac.
- Click on Windows or Mac and log in with your ULID and password if prompted to do so. You will be directed to a form to request the download file be sent to you. You will need to fill out the required fields in the submission form. Once submitted, your request will be handled in the order it was received. Once approved, you will receive an email. You will then click Download Files and you may be navigated to a Central Login page where you will need to enter your ULID and password. Once you log in, click the file next to Attached Files.
NOTE: If you have never access Liquid Files (SendTo) before, you may see a log in page to log into Liquid Files itself. Instead, you will want to click the SSO Sign In button to be navigated to a Central Login page. You will enter your ULID and password. Upon logging in, you will need to accept some terms and conditions. Once you have done that, you will never be prompted again for an SSO sign in.
- Upon successfully downloading the installer, you will need to open the installer and follow the prompts. When you get to the Installation Type screen, ensure that only the VPN checkbox is selected, then click Continue to proceed with the installation
Cisco Anyconnect Disable Automatic Selection
Figure 11:

- Click Continue to finish the installation. Once finished, open the Cisco AnyConnect Secure Mobility Client. You can find it in the Cisco folder in your applications, or can be manually searched in your Launchpad, as instructed above.
Figure 12:
- Type VPN01.ILSTU.EDU in the empty text field, then press Connect.
Figure 13:
- Enter your ULID in the Username field and your current password in the Password field. Click OK.
Figure 14:
- You will see a welcome window. Click Accept to be connected to the VPN.
Figure 15:
- Now that you are connected, you will be able to access university-restricted applications such as iPeople.
- When you are ready to disconnect from the VPN, go back to the application and click Disconnect and close out of the application.
Cisco Anyconnect Automatic Start
Figure 16:
How to Get Help
For technical assistance, you may contact the Technology Support Center at 309-438-4357 or by email at SupportCenter@IllinoisState.edu.
Cisco Anyconnect Startup Disable
Back to Overview:
Remove Cisco Anyconnect From Autostart
Related Articles:
